Exploits are back! I forget, are hacks a sign of bull or bear market?
The Anyswap network had become a popular low cost method for bridging tokens.
Anyswap v3 launched just over a month ago, offering innovative cross-chain liquidity pools. Unfortunately, a flaw in the new protocol was exploited over the weekend, and a hacker (0x0aE1554860E51844B61AE20823eF1268C3949f7C) drained $8MM across Ethereum, Fantom, and BSC. Users of v1 and v2 are not affected, and Anyswap announced v3 LPs would not incur any loss.


What exactly happened? Let’s talk about a different type of Curve than we usually discuss. Elliptic Curves!
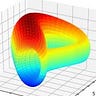
People like to brag that cryptocurrency is “secured by math” but often don’t talk much about the actual math involved. Elliptic curves look like the funky horseshoe shape above and are easily calculated as the set of points satisfying a simple equation:
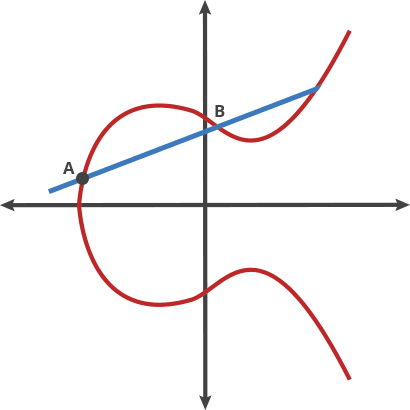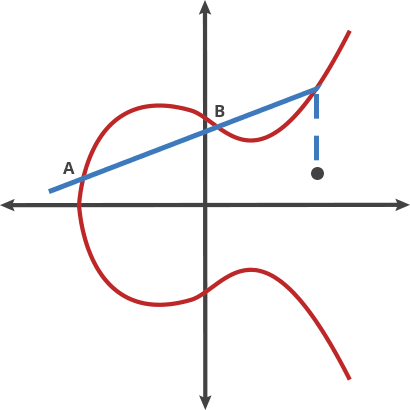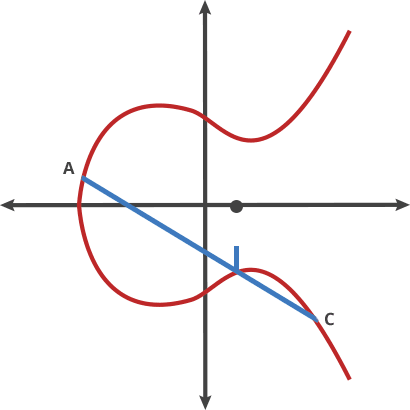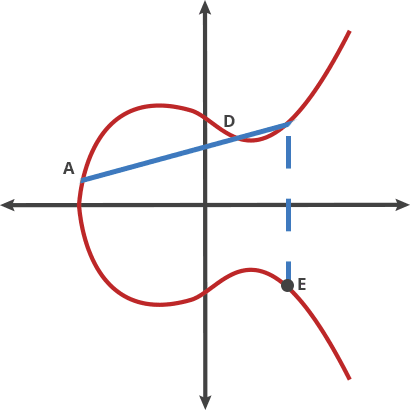
These curves have the nice property that any non-vertical line drawn between two points on the curve will intersect with, at most, one other point. This makes them useful to produce asymmetric key pairs.
Asymmetric key pairs have to be easy to generate but difficult to verify. The process of Elliptic Curve cryptography is to use two points to find the unique third point generated from this pair. Use the result to derive a few related points in a deterministic fashion. The process is iterated some n time to land at a final point. As it turns out, if you are given the first point and the final point, it’s mathematically difficult to calculate n, the number of trips you had to take to get between them. Yet it’s easy to verify — exactly what we need for asymmetric key pairs.
The process looks as follows, from Cloudflare’s more thorough explainer:
This is the guts of the ECDSA, the Elliptic Curve Digital Signature Algorithm. The specific steps are outlined as follows per Wikipedia:
Wikipedia goes on to note that “it is not only required for k to be secret, but it is also crucial to select different k for different signatures, otherwise the equation in step 6 can be solved for d_A, the private key. This method of attack was described as far back as 2012. If you happen to reuse k, it becomes easy to solve for the private key and directly drain the wallet.


It just so happens Anyswap v3 committed exactly this mistake.



Anyswap quickly fixed their bug, although experts noted that this patch is itself a bit patchy.



The preferred solution would be a deterministic nonce.


This simple solution may be scoffed at by British people, who recently took to sniggering at the common term nonce. It turns out that in their confusing dialect of “English” a nonce refers to nutters who fancy shagging sprogs. Blimey!

Fortunately for all involved, the $8MM hack was relatively small and Anyswap alleges no LPs will lose funds in the incident. Nonetheless, it’s always disconcerting when old security holes are exploited. It’s almost as if we’re doomed to keep repeating the same mistakes over and over again…


For more info, check our live market data at https://curvemarketcap.com/ or our subscribe to our daily newsletter at https://curve.substack.com/. Nothing in our newsletter can be construed as financial or technical advice. Author is a $CRV maximalist, has no position in Anyswap and does not speak British.