What a catastrophic weekend. So many of our frens and favorite protocols got devastated, as a zero day Vyper bug was exploited as hackers drained four Curve ETH pools.
The specifics are a compiler bug in Vyper versions 2.15 through 3.0, allowing a reentrancy attack for pools handling raw ETH. Fortunately, very few Curve pools used this version, but unfortunately they all got rekt.
First in the morning was JPEG’d
In the fog of war, the reentrancy bug was still unknown, and there was some thought it may have been a faulty implementation. But then, Metronome fell…
Amidst the fog of war, it became clear that something out of the ordinary was wrong. Adding to the tragedy was white hat hackers racing against the black hats and losing in photo finish races.
In the case of Alchemix’s alETH, the heroes identified there was in fact a bug and moved to withdraw, but only got 2/3 of the way through before a hacker drained the remainder of the funds, causing a loss of ~5000 ETH.
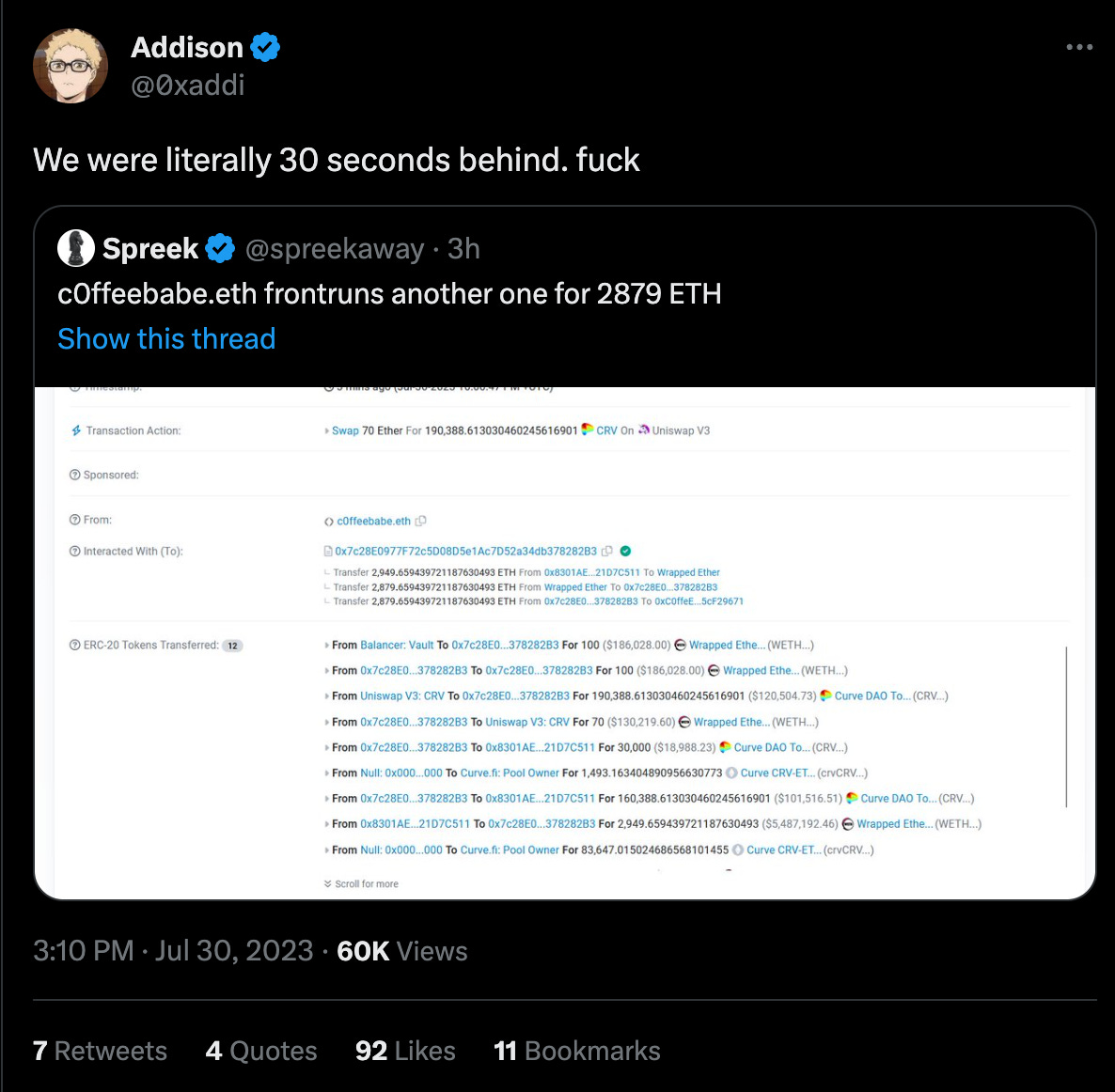
The grand finale was Curve’s primary onchain source of liquidity, the CRV/ETH pool. At this point the white hats had figured out the pattern and were working to save it, but lost out by minutes.
This hack on CRV/ETH left the DeFi community in a state of panic. For starters, the broken state of the pool messed with the Curve UI and router. This had many unfortunate effects, including displaying wildly incorrect information about the $CRV price — with some believing the $CRV price had plummeted to $0.10
This led to its own tempest in a teapot as users concern trolled about Mich’s mathematically difficult to liquidate $CRV position. He rebalanced amidst the crisis to at least stem this FUD, which we consider to be largely inconsequential concern trolling.
By this point, the CRV/ETH pool was damaged, but still had some funds parked within it. So the race was on for the final funds in the pool. Yet again, the white hats missed out by a slim margin.
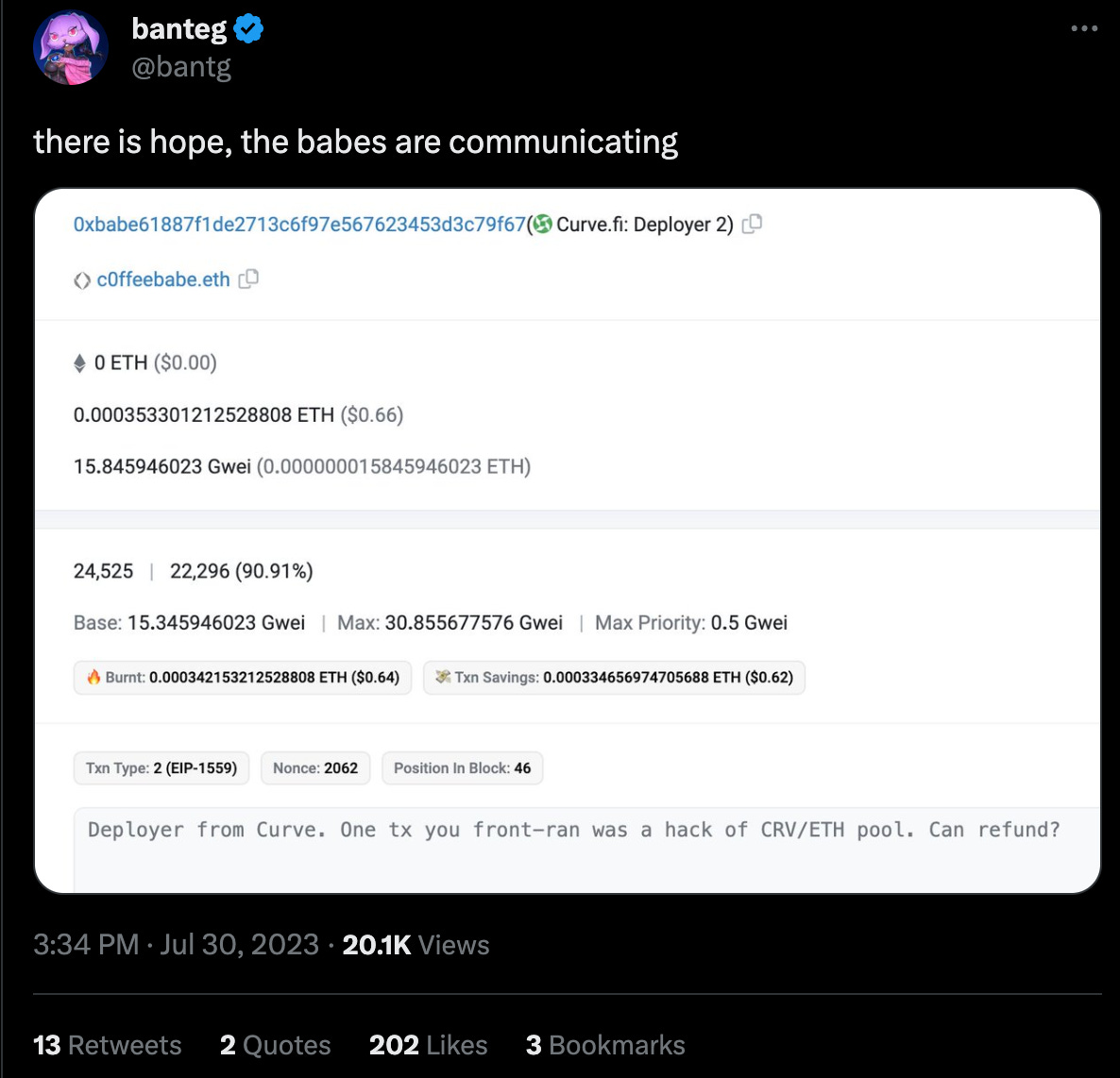
Fortunately, in this case the front runner was also a true babe. The 0xbabe Curve deployer address had a quick chat with c0ffeebabe.eth
And this message apparently did the trick…
So what next? Curve has cautioned exiting Arbitrum TriCrypto. Although no attack vector has been identified, it fits the profile of a vulnerable pool (using older Vyper and handling raw ether).
Overall around Curve, massive liquidity is exiting out of an abundance of caution. Frax in particular is removing funds with plans to conduct a security review before they consider redepositing.
We would not blame you if you do the same — we’ve also taken this precaution with some of our larger bags, although we plan to redeposit.
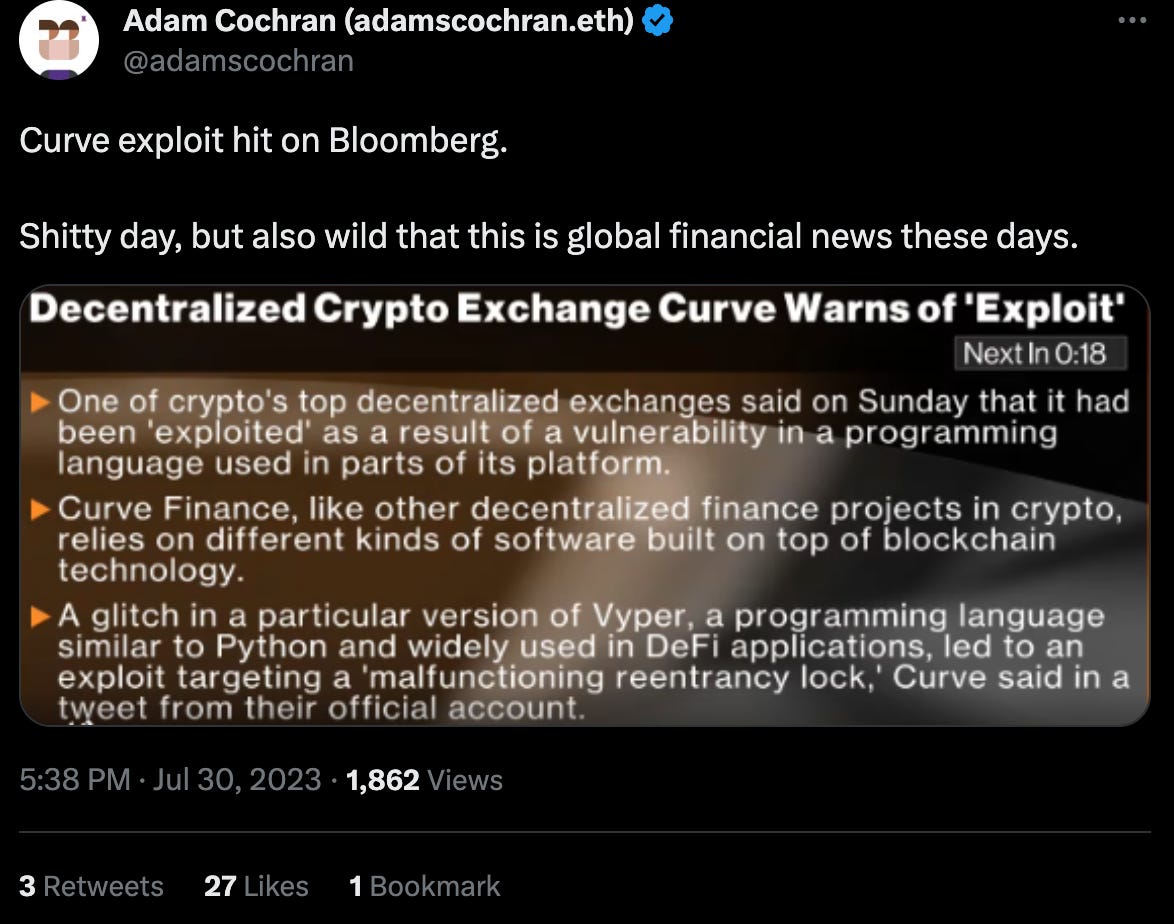
We also expect further tumult, because the normie news will be slow to pick upon this story, and we may expect further dumping. We’re expecting choppier waters to come (NFA).
For comprehensive news, we recommend Leviathan News, for which we joined two extensive Twitter Spaces (1 | 2, coming soon to YouTube?) the night of the attack and a large panel discussion on the livestream this morning.
There is a ton of soul-searching occurring right now. Many questions about best security practices in the aftermath of this. We’ll punt much of this discussion to upcoming newsletters, but first a few high level thoughts on Vyper.
A lot of people are looking to finger point at Vyper, but this is wholly misplaced in our opinion. Attacks like these demonstrate the need for more compiler diversity, not less. Compiler engineering is badly underfunded, understaffed, and underpowered. Nobody funds this type of research because there’s no returns to be made in more secure compilers. They’re open source projects that require top tier devs to work on it as a passion project. And they’re expected to secure our entire ecosystem?
Vyper has maybe 1-2 devs on a good day. The project was founded by Vitalik and would be the sort of public good infrastructure one might expect should properly be funded by the Ethereum Foundation, and yet they’ve not opened their war chest to do so. Much of the funding has come from Curve, who has been screaming loudly about the importance of more entities stepping up to do so. One obvious step in the aftermath is that we’d hope all compilers, not just Vyper, get a boost in funding from the community.
While Vyper’s reputation has taken a hit, the existence of a malfunctioning reentrancy guard obscures the fact that on newer versions of Vyper, this protection has worked very well and is an immensely useful feature that shows off Vyper’s focus on security.
For more technical discussion of what specifically happened:
Finally, we know absolutely nobody wants to hear this, but it’s a remarkable stress test for crvUSD, which remains remarkably on peg despite the stress affecting the rest of the protocol and a fearful exodus of capital.