LinkedOut! 🕵️♂️🚓
The case of the spear-phishing hijack
Author’s Note
Been too long, frens! Had to return because this story was too wild to not be cataloged…
Last month, my LinkedIn profile was hijacked and abused for a highly targeted spear-phishing attack. After a monthlong ordeal, I eventually recovered the account thanks to an assist from a colleague at the FBI.
I wrote up this detailed post-mortem so OPSEC-maxis can have all the relevant details they need to protect themselves.
Since very few people have time to read, here are some bullet points summarizing the highlights of this mystery:
On October 9 at 1:19 AM, my LinkedIn account’s password and 2FA were hijacked in under a minute, from IP addresses originating in Pittsburgh, CA and Hanoi, Vietnam.
The attacker used the account to message dozens of selected high-value contacts before support froze the account permanently.
Mitigation and full understanding of the scope and method of the attack was complicated by difficulty reobtaining access to the account.
Scams and hacks are already prevalent, but as we zip past the AI singularity their complexity and sophistication will only multiply.
It’s always a good time export your contacts and review your security settings.
During the chaotic month, when it appeared I might be permanently locked out, it was challenging. Even though I’d scarcely used LinkedIn since going all in on crypto, the legacy network continued to demonstrate incremental value from the years I’d invested into it. LinkedIn effectively has a monopoly in its space.
While pondering how to replicate its value if I got locked out forever, I prototyped the concept of “Handshake,” as a way to better control your social graph by attaching paid refundable bounties to inbound message attempts. Details in the post below, but the impatient can check out the early demo here.
At any rate, I enjoyed compiling this extensive post-mortem. Can you solve the mystery of the account hijack faster than I could??
Covert Ops
Hello, my name is Gerrit. I don’t exactly hide this fact, nor do I tend to broadcast it. But let me take the opportunity to properly introduce myself.
As longtime readers may know, I’d been softly working under the pseudonymous “CurveCap” as some light personal OPSEC. Scams are so rampant nowadays. For my years in crypto, it had previously proved prudent to add some slight friction to uncovering my personal identity. This strategy worked for quite some time, but as my pseudonym grew in cachet over the years, my cover’s finally been blown.
How did I find myself in the crosshairs?
Lately I’ve had the opportunity to speak at increasingly higher profile conferences to spread the word about Curve, crvUSD, stablecoins, and DeFi. Requesting organizers only refer to me pseudonymously in writing was a complicated instruction for weary event organizers. In hindsight, this precaution proved less painful than what would happen after it was ignored.
Two months ago, one event’s organizers accidentally published my real name. As I’d feared, over the following days I was inundated by a plethora of “attempted password reset” emails to any service registered to my name. I don’t know what they were planning to do with an empty Instagram feed I forgot I’d ever registered, but I’m glad I didn’t have to try and unsee it.
The fact that the attacks were becoming more concentrated was unnerving, but it didn’t seem there was much I could do. Should I really care if they overtake a long abandoned and immaterial account?
I tightened security on a few core accounts related to personal finances, and prayed to weather the storm.
LinkedOut
At 1:09 on October 9, I received three emails in such rapid succession it was impossible to actually determine the exact order of the sequence.
Your LinkedIn account password has been changed (Pittsburgh, CA)
Your LinkedIn 2FA code (Hanoi, Vietnam)
Your LinkedIn 2FA settings have been updated (Hanoi, Vietnam)
At 5:39 AM, far from any of those places, I noticed the exploit. After a month of escalating attempts to steal my identity, the hackers had finally succeeded.
At first I didn’t think them swiping a LinkedIn account was terribly relevant. Having mostly worked pseudonymously of late, my LinkedIn profile had been in a sorry state of neglect. “Take it!” I thought. “It’s your burden of wishing contacts a happy birthday now.” Yet by the end of the month, I’d not only come to appreciate the account, I’d be arguing how many millions of dollars it is worth.
In the moment, I was far more concerned with the assumption they performed the hack by getting access to my Gmail account. Google has decent security, and my account is locked down so tight I often struggle to get access to my own account when I’m traveling abroad. A thorough security review showed nothing untoward, so I wondered how it was accomplished so easily by what appeared to be a VPN.
I dutifully reported the account as hacked to LinkedIn support. They quickly locked the account and provided a link to complete identity verification. The straightforward process left me reassured that this might be routine, and it might be restored within a few business days.
At 2:54 AM the next morning, (“Do they never sleep?”) the identity verification was complete and they sent a password reset email. It was set to expire in 24 hours, so I ignored it while I fought more urgent fires. I expected I could attend to the matter during the lunchtime food coma. Before I could break my fast, though, I got an urgent DM.
“Gerrit, I’ve traded messages with you on LinkedIn. Was it actually you reaching out?”
I zoomed in on the screenshot
Gerrit • Active now Hi Bob, I’m glad to connect with you. How’s your work going Lately?
Bob • 12:14 PM Wow. You wrote me in 2015. My apologies for taking ten years to respond…
Gerrit • 12:49 PM Thank you, I’m fine, Bob. I have a female entrepreneur friend who currently manages her own family foundation. During our conversation, she mentioned advisors. She also needs to build some elite connections in this field. Are you interested in getting to know her?
This message was alarming for many reasons. Chief of which is that I didn’t actually know Bob’s real name (for the hackers who are likely reading this, Bob is not his real name), I’d only known him from his anonymous Telegram username. I didn’t even have any idea we were even connected previously on LinkedIn.
Bob is a very high net worth individual. I’ve had the pleasure of interacting with him mostly anonymously. He once trusted me enough to do a screenshare about a question he was having, during the course of which he casually made a “test transfer” of 5 BTC (which at present would be worth nearly $1MM). He operated almost entirely anonymously. I had no idea I was connected with this whale or that his real name was Bob. So how did the hacker sniff him out so quickly?!?
The hacker had not only hijacked my LinkedIn profile, but had very quickly executed on a sophisticated plan to seek and out spear-phish (or depending on your reading, to catfish) at least one highly anonymous individual. Was it random? Or had they done this all to single out this particular Bitcoin whale in a hunt?
The issue was clearly urgent, so I dropped everything to solve it. I sent messages to a handful of other LinkedIn users I thought might be targeted in such a scheme, but they reported they hadn’t seen anything from me.
I quickly hunted down that “Password Reset” email to try to lock this down immediately. To my horror, I clicked the link only to find out the link had already been marked as “expired.”
Except, I had never clicked the link, a fact I quickly confirmed in my browser history. How had it expired already?
I reported this all to LinkedIn immediately, as it was clear from the timestamps on Bob’s messages that my account was in fact still active and being used maliciously.
𝕏-communicated
Here things took a turn to the worse. My interpretation of the situation is that the service desk at LinkedIn was also unsure what was going on, and decided it was simpler to close my account than to investigate. Whatever the reason, from this point forward, they only declared my account had committed “numerous violations of their community policies” and would be “permanently restricted.”
Permanently restricted???
Surely they were joking. I tried to explain to service team that I’d had the account for so long it was old enough to drive. I’d been among LinkedIn’s earliest adopters and a vocal advocate for the duration. I’d never had so much as a strike reported against me.
Moreover, I’d hardly even used the account in years. The only possible “violations” would necessarily have to be whatever the hacker had been doing with my account. I saw the one phishing message, but who knows how many more of the thousands of contacts they’d also harassed. I needed to find out the scope of their actions, and the only way to uncover this information was to regain access.
Unfortunately, at this point, it didn’t matter what I said. Once one customer service agent had declared it “final,” no other agent would bother touch the case. They would simply restate their usual refrain… “our Safety Team has already been in touch with you via case (251011-002984), and they have made a final decision.” Over the next week I’d continue opening similar customer support threads until it was clear the help desk was a dead end.
I decided to escalate and pulled out the playbook from the mid-2010s. I presumed I was still operating in an era in which customer support agents will disregard you unless you can make some social media noise. Let’s get this to Reid’s attention! My footprint is relatively small, but I have pull with some bigger accounts.
As it turns out, 2025 is not 2015. Nowadays, customer service bureaucracies have grown so thorny, even social media clout can’t penetrate the thicket. After raising a minor tempest on 𝕏, I thought reaching a real human awake during US hours would be my salvation. I laid out the case and all the evidence, sure they’d help out. Until I ran into the classic mantra...
“Our Safety Team has already been in touch with you via case (251011-002984), and they have made a final decision.”
“%&$#,” I disclaimed loudly, while also swearing I’d get my account back. With the customer support route thoroughly exhausted, my path to recovery grew more limited.
I needed to find a mutual contact at LinkedIn. In my days I’ve known dozens of people who worked at LinkedIn. But who still works there? And how to get their contact? In the before-times, within one minute I could search mutuals on LinkedIn and surface contacts within minutes. But… no LinkedIn, no network effects.
Maybe I could go the legal route, I must know a hundred lawyers… all I need to do is do a quick search on LinkedIn and… rats, foiled again!
The first time I needed the network this decade, and it’s gone!
My only choice was to start cold texting classmates I hadn’t contacted in years and begging them to run the search on my behalf.
“Yes, but if you say your phone has been hacked, how do I know you’re actually Gerrit. What was my roommates’s favorite food?”
After some grueling identity probes and light socialization, I managed to surface three current employees at LinkedIn spanning the tech and legal departments. Finally, real human contacts would solve this case.
Best Served Cold
Another week passed. My hope that internal contacts at LinkedIn could crack the case dissipated. I didn’t expect any of them would turn full-time detective on my behalf, so I forgave any second degree connections who went quiet. But my curiosity was piqued when one reported back simply that he wouldn’t be able to help, and then stopped replying to any follow-up.
Who got to you???!
My paranoia intensified. To this point, I’d assumed the attack must be something prosaic… a relative anodyne security lapse I’d simply missed. But why’s the trail going cold? Why were people refusing to help? What if it was something far more sinister...
Had they exploited LinkedIn support from the inside? Or perhaps my computer had a screen logger that was able to read the 2FA code from an open Gmail window? Or had my phone been hacked by the Chinese government on my recent trip to Hong Kong? Had the drone I saw outside my house been secretly hacking my WiFi?
Or even worse, what if I was suspended not for the hacker’s actions but for my own checkered past. Perhaps customer service simply decided to look at my activity and decided my presence really was polluting their platform.
Especially in my younger days, I’ve a long record of tiptoeing over the line. In truth, I have no pretenses whatsoever to being a good person. Quite the opposite, I identify proudly as a scumbag. In my time I’ve enjoyed both poker games and cigars, if never simultaneously. I often have untoward thoughts… lust, wrath, and all the deadly in-betweens. I associate exclusively with sinners. And get any of my ex-girlfriends on the stand, and you’ll have enough dirt to force me into a low wattage electric chair.
If it’s to be a purity test, could anybody prove sufficiently divine as to enter the kingdom of LinkedIn???!??
I kept turning over all my recent activities… anything worth giving me the boot? I liked some friends’ posts about crypto, but if this is such a crime, shouldn’t they be the ones banned?
I had dug up a few connections to meet on a trip to Korea, but it was the southerners, not northerners.
I had gotten a former student a job when he asked for a connection… a crime against the narrative that AI is decimating jobs?
After comparing my behavior against LinkedIn’s own terms of service, I judged that an impartial jury would probably find in my favor if it ever got so far. More realistically, I imagined probably I could resolve this in mediation, as long as I was willing to rack up enough billable hours to make this worth a lawyer’s time. It was obnoxious I might have to spend out of my own pocket when I was the victim, but life is seldom fair.
Thus began my arc of trying to recruit a lawyer. I researched many different law firms and tailored different pitches to try to fit their narratives. To Dhillon law, I spun this as a social media deplatforming. I played up a hot stablecoin narrative to a cryptocurrency focused lawyer.
It didn’t matter though. I’d learn that there was no amount of money I could tease that would get a lawyer willing to deal with a customer support department, as one group chat memorialized while laughing me out the exit.
Unpersoned, unrepresented, and unable to even birb my way out of the situation. I keep hearing complaints that the economy is bad, yet nobody’s willing to pick up the free money I’m desperately dropping right atop the table?
Very well… if nobody’s willing to accept money from a social media pariah, I’ll let AI replace your jobs for free. I’ll build my own lawyer!
I got busy training different algorithms against each other to simulate my case, which briefly provided me a glimmer of hope. Asking them to arrive at a fair value for damages, dueling LLMs got into a heated debate… “No… $1MM is too conservative…” “$4MM”... “$6MM”... I’d started an AI bidding war!
Maybe if I dangled these numbers in front of the real lawyers it might get their attention…
Fueled by a rush of endorphins, I oneshot LinkedIn’s legal address a sternly worded “Notice of Preservation” in anticipation of expected litigation. That ought to get their attention! To my delight, they replied within a few minutes.
“We have a portal for receiving data requests from law enforcement.”
Law enforcement? Very well, we’ll escalate this to the proper authorities, but let the record show this was YOUR idea, not mine.
Interlude: A Handshake Agreement
Somewhere around the time I mentally began valuing my LinkedIn profile in the millions, I began to earnestly imagine how my future might unfold if I never regained access to my multimillion dollar network.
Rebuilding from scratch on LinkedIn under a new account, yes, I might reconnect with several classmates and maybe regain 20% of my prior connections. A lot would simply be gone forever. By the time I got back to where I’d built it to today, I might be retired. Nor would it make any sense to rebuild my network on a platform that had already swept the rug out from under me once for the trivial offense of becoming the victim of identity theft.
It felt eerily like dying and getting to watch your own funeral, except in this case you were simply erased from the hivemind’s memory. I took many a brisk October walk as I earnestly contemplated how I might move forward with my life.
Naturally, an onchain solution could help people to fully own their networks, but too much of the professional world still utterly despises cryptocurrency and would never touch such a solution. To build a network among the nocoiners, a viable service would have to trojan horse web3 principles via web2 branding.
I also imagine the “own-your-data” pitches will fall flat. The number of people who are livid about losing access to LinkedIn is way too miniscule to gain traction. Deplatforming is more an issue on politically charged platforms, not the sanitized HR-compliant discourse of LinkedIn. Even most DeFi nerds don’t even care if something is truly decentralized. There’s no real pitch to be made on “owning your social graph” that could catalyze enough people to boostrap a new social network.
I wrestled with the dissonance. On the one hand, LinkedIn certainly has a monopoly on a service with real utility. On the other hand, I’d also gone about five years without needing them, and outside of this weird edge case my daily routine was unencumbered by the loss. One missing data export and I wouldn’t miss it.
Perhaps there’s a better way to organize the vast world outside LinkedIn?
Then I noticed… even though I’d been disconnected for nearly a month, I was still receiving cold emails that referenced some obscure detail on my LinkedIn profile. Maybe they’d scraped it illicitly, or maybe they’d paid LinkedIn their fair due. But were they actually still monetizing a user they’d rudely unplugged?
Although I’ve never been bothered by spam, it occurred to me others might place a higher value on their attention. And then I though, this could be the answer… a reachability network.
You grant access to the profiles you keep current, be it LinkedIn, X… and then let the platform gatekeep for you… for profit!
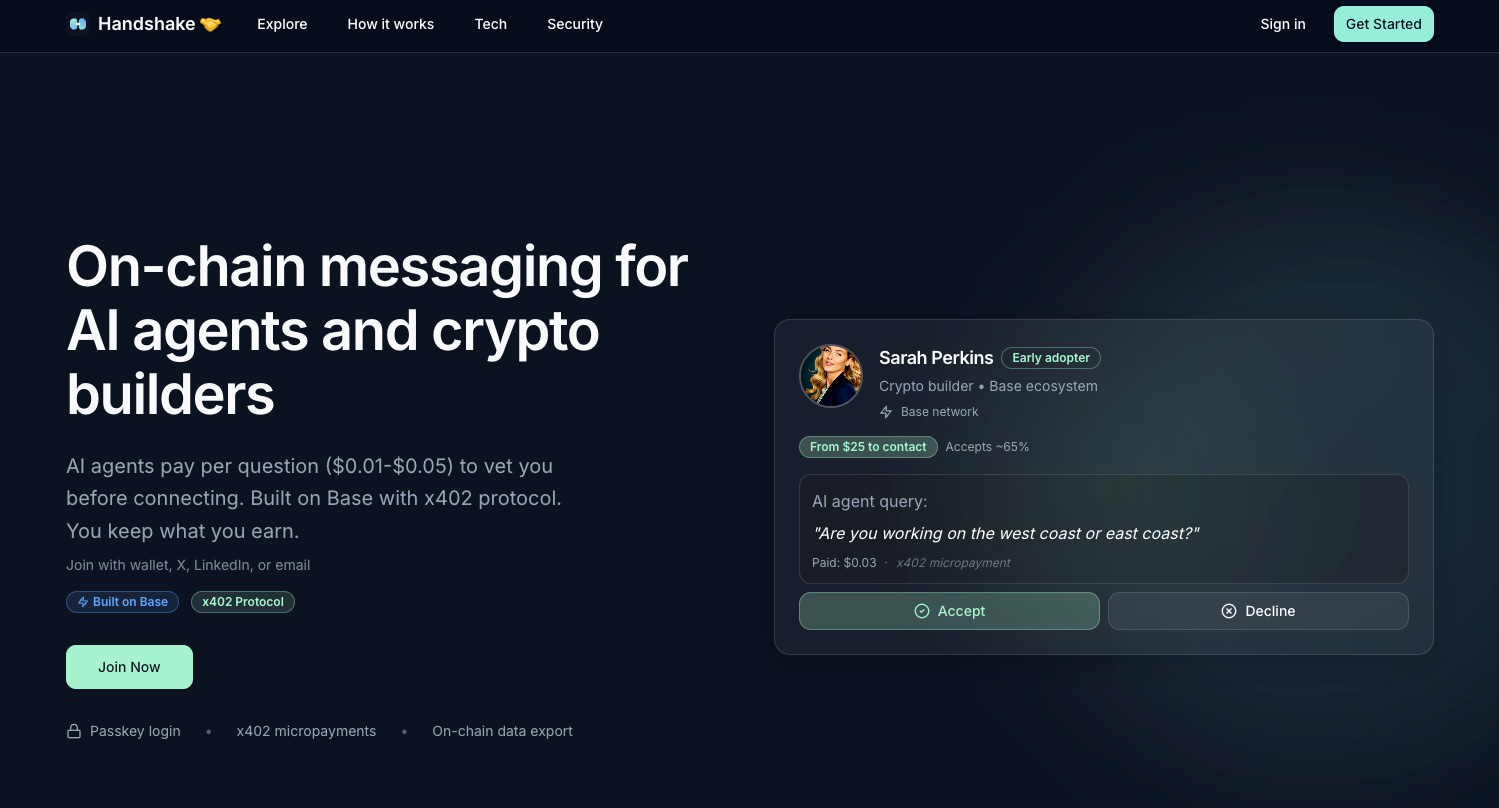
LinkedIn captures the full value of your attention for themselves and return none of the profit to you. In a web3 model, you would retain this full value. You’d link your profiles and set your price for contacting you.
The current version lets solicitors attach a dollar bounty to their message. If you don’t read past the subject, you keep the bounty. If it’s so important you’re willing to read further, the solicitor gets their bounty refunded. Powerful networkers deserve whatever their attention is worth.
I (well… Cursor really)… prototyped a super basic demo, codenamed “Handshake.”
It’s a model that works very well with the direction the world is heading. Before next decade, humans will outsource their prospecting and gatekeeping to AI agents. They’ll give their agents a budget and task them with drumming up profitable leads. Meanwhile, your agent will charge the inbound bots to negotiate and titrate access on your behalf. A series of microtransactions on a cheap L2 later, and you’ve optimized each user at the perfect balance of reachability and rewards. But we’re getting ahead of ourselves…
If you think it’s an interesting concept, please register an account and drop a note! Just beware that the functionality is extremely minimal at the moment so don’t be too angry if features don’t work as intended…
The Long Arm
By this point I was beginning to feel like I was running out of options. Moreover, nobody really seemed to get why I cared about LinkedIn of all networks. Some people are excited about TikTok or Snapchat… but LinkedIn is nothing but boomers, right?
It also happened to be the only social network I’d ever bothered to invest time into since the outset. I’d always felt the other socials were overhyped. I’d basically ignored Facebook (now Meta) and Twitter (now 𝕏), but directed everybody I met at a thousand cocktail hours to connect on LinkedIn. As an active and consummate networker, I’d spent decades building a robust network of thousands of contacts, giving me a top 1% network.
Over the years, to my great discredit, I’d effectively disregarded friends and family all in the pursuit of growing my LinkedIn network. Then it got ripped away. They didn’t even allow me to export my connections as they kicked me to the curb.
If I couldn’t get reinstated, I could maybe get even.
A friend pointed me to the team at Groom Lake, a private security company founded by former three letter agency officials. I took my chances that the “three letters” were one of the more relevant alphabetical permutations (ie more NSA than NEA).
We had a great chat, and they even seemed quite impressed by some of the paranoid measures I’d taken to prevent against obscure attacks like sim swaps. They prepared an eminently reasonable quote for some background checking into possible suspects I suggested, but confided there was nothing they could do to bypass the dreaded ToS checkbox and get me a direct line to LinkedIn.
While I thirsted for the perp to be brought to justice, I held out for more intel. I knew the missing piece of the puzzle had to exist somewhere in LinkedIn’s servers. Just a peek into the account might crack the case without needing hired guns.
As I’d been collecting evidence for my lawsuit, I’d also filed a report with the FBI. Of course, I never expected the nation’s top law enforcement agency could be bothered with something as trivial as an account takeover. They have serious crimes to investigate, and nobody’s getting the corner office for cracking the case of the social media bandit. All the same, I filed a report just so I might start a paper trail.
I got a call from my friend Nick, who had previously referred me to a colleague at LinkedIn and was genuinely curious if there were any updates. I recounted all my increasingly unhinged measures… attempting to self-file a lawsuit… submitting complaints with two states’ attorneys general… reporting the incident to the FBI. Here he stopped me cold.
“You know our former classmate is at the FBI, right?”
Actually, without my LinkedIn profile, I don’t know have the foggiest idea what anybody’s doing…
But pretty quickly I was able to get on the phone with the old dormmate, and we caught up as if no time had passed between then and now.
He recounted the important work he was doing… he was in the middle of busting up a massive “pig butchering” scheme in which 80-year old ladies were being defrauded of their entire life savings. We lamented how much worse scams are bound to get in the era of AI. Even before general intelligence, the agency was inundated with the worst behavior you can imagine.
“Well, this is a $6 million case!” I almost blurted out, before settling on a tamer line, “At this point I don’t even expect to get it back, but I’d like to know how it was done, if I’m at risk, or if anybody else was impacted.” To my surprise, he expressed that he’d be delighted to poke around.
Four hours after I got off the phone, LinkedIn restored my account fully.
Case Closed
For all of October I’d been kept in suspense about how the perpetrator committed the deed, as well as the extent of the crime. Based on the pattern of evidence, it seemed like they must have gained access to my email, or something far more sinister.
Have you already cracked this case, gumshoe?
As soon as I got my LinkedIn account back, I surveyed the damage and pretty quickly was able to deduce exactly how everything happened.
Little did I realize, there was actually a second email address registered to my LinkedIn account. Some time ago, at a failed startup I’d long since suppressed from memory, I apparently added a secondary email to LinkedIn for reasons I can no longer fathom.
Exactly one day before the exploit, somebody had purchased the expired domain name. They were able to use this email to trigger a 2FA reset and claim ownership over the profile, presumably finding the password leaked on the dark web or something.
When I reported the profile had been compromised, both of us were locked out. After completing identity verification, when the account got unlocked, the password reset request went to both my real email and the compromised email. They were quickest to reset the password, and then proceeded to cold solicit 43 colleagues before the account got permanently restricted.
It might have been mitigated if the account recovery process asked me to confirm email addresses at the time of identity verification, but this was surely too obscure of an edge case to ever merit serious consideration.
Although it was not as bad as my worst fears, it was nonetheless a moderately sophisticated hack to execute. They had to spend a hearty $18 buying the expired domain name (the day before the attack) just to target me directly. I still don’t know how they figured out the long dead startup was connected to my LinkedIn, so they clearly did some homework and thought they’d get a good return phishing my colleagues. Maybe their AI also valued the profile in the millions?
Most importantly, there was no lasting damage. Most of the targets ignored the message, or never saw it before it was flagged. One had no idea who I was and requested we unconnect. One guy, now CEO of an “AI native programmable cloud factory,” missed the spam message, but took the opportunity to reply to a cold solicitation from five years earlier. He answered in the affirmative, so in a way the hacker only benefited me with a little deal flow!
If I didn’t happen to have a contact at the FBI, I might never have recovered the profile. Maybe a judge would have taken pity on me for a sloppy attempt at self-representation, but I’m grateful it didn’t need to go so far. It was very lucky my network was good enough as to unearth a friend in such a high place, so in the future far better to be careful.
I’d urge everybody to take a little time to review your security settings, if you become the victim of identity theft, you might be victim of either the hacker or an overly byzantine customer support process. You can and probably should export your data on a periodic basis.
For my case, I lost $12 in certified mail expenses, but I rekindled stronger connections with several connections in the process. And I retrieved a profile valued by some at millions of dollars… any protocol out there willing to let me borrow against it? Most importantly, I’ll remain eternally grateful to everybody who helped me out when I had nowhere else to turn. A bad experience that ended up a net positive.
If I learned anything, it’s that I’ve spent too long trying to protect my identity from the evildoers. This strategy might have worked for a time, but it’s backfiring when my enemies can track me down but my friends cannot. But I only got out of the mess when my direct personal network stepped up to help out. Much like currency, perhaps identity also needs velocity to realize value.
My takeaway is that no precautions can ever protect us from the hacks and scams. Our only hope is investing time and energy into growing our community, who are the only people who might help when life strikes.
I for one plan to be much less cautious going forward about dropping my real name in public. With just one lifetime, none of us have time to live modestly. I’ll fully throw myself into the mercy of the public arena, and hope the forces of good continue to outweigh the forces of evil in this eternal cosmic battle.
If you read this far, I’d encourage any of you to help join the fight, by connecting with me at my LinkedIn (will accept all incoming requests for the next 24 hours as thanks for reading)… or better yet… my new Handshake account. 🤝




Thank you, Gerrit. It was very educational and provided a lot of important insights. I appreciate how clearly you explained the events and your experience. It's a valuable read, especially for anyone looking to understand how to prevent similar issues. Your work is really appreciated!